The website’s lack of security will lose customer trust and seriously affect the reputation of the brand. The development of e-commerce sites entails many security challenges, hindering the development of businesses. Let’s learn with VNETWORK about common website security errors and how to secure websites, to limit risks for businesses.
What is website security?
Each website has a separate server, also known as a server, and is connected to each other through a private IP address, which is encrypted and secure. However, if one day the website is hacked, how much effort and construction time will be lost? The website will be severely affected in terms of reliability, performance, and quality of service. At this point, you need to immediately implement more in-depth solutions to secure your website.
A website can operate well and smoothly, so it is necessary for administrators to regularly perform security enhancement activities, in order to avoid any bad effects affecting the website.
Website security error
You’ve made great content for your website, and you’ve shared that link on your social media and with your friends. But when they click on it through browsers like Chrome or Firefox, it shows that your site is not secure and won’t allow anyone to access it.
Some users may open your site, but show the ‘unsafe’ label in front of the domain name. Sometimes this problem can appear randomly on a website that has been working fine for a while. You don’t know what to do other than resolve this problem.

Your site is showing an ‘unsafe’ label in front of the domain name
Common website security errors
VNETWORK has compiled a list of the 10 most dangerous website security mistakes that businesses should avoid.
1. Invalid Input
By not validating what input and content are uploaded, the website is vulnerable to attacks such as cross-site scripting (XSS), SQL injection, command injection, and security attacks. other. Input uploads must be authenticated from both the server and the end browser. Typically, businesses only validate input from the browser end, without validating server input, resulting in malicious/malformed data/scripts running on websites and databases of the system.
2. Infrequent or no site security scans
The importance of regular website security scans is overlooked by businesses. Only through regular scanning can we find vulnerabilities, and fix them. Businesses often make the basic mistake of not scanning their website every day or after updates on business policies, systems, etc.
3. Authentication and permissions
The administrator password or the password to the server is set very lightly, with types like admin, 1234, or other commonly used words. They can be easily cracked with password-cracking programs and if the password is cracked, the website will be compromised.
Do not enforce strong password policies and multi-factor authentication for website users. When a site allows users to continue with default passwords, or weak passwords without reverting to password expiration or relies solely on unidirectional passwords for security, the organization is making the system itself. Your system is vulnerable to breaches and attacks.
Easily giving admin rights and privileges to end-users and external organizations leave the site vulnerable to attack.
Changing the folder and data file permission structure follows advice from the internet to fix permissions errors, but in the end, you’re opening the site up so anyone can change the configuration. structuring, modifying the code, and running malicious programs on your website.
4. Unincorporated Security Measures
It often happens when organizations and web developers don’t think about website security as a whole and, therefore, apply unconsolidated security measures. For example, they might use a website security scanner but not a Web Application Firewall (WAF). So the vulnerabilities and gaps are effectively identified by the scanner, but the website remains vulnerable until the vulnerabilities are fixed (it took more than 100 days even for web browsers). critical vulnerabilities) or developers are focusing on patching the site instead of fixing the vulnerabilities.
5. Homegrown security methods and algorithms
Many organizations still often have the misconception that self-development is better and that they are more secure because attackers are not familiar with their own types of code. So they used security measures in their own way. This only increases the probability that vulnerabilities and vulnerabilities can be easily discovered by attackers and the bots they use. It is better to use methods and algorithms that have been thoroughly tested.
6. Outdated software with known vulnerabilities
Some developers still use components that are known to have security vulnerabilities such as unpatched third-party software, outdated plug-ins, open-source components, untested code, and copy, etc will make the site insecure, weak, and vulnerable.
7. Not tested on a regular basis
While site scans need to be done daily or after major system updates, it’s not enough. It is essential to test every bit of code, software, updates, and components on a website. Additionally, quarterly penetration testing and security assessments by reputable experts are essential. This will ensure that your website is secure and your users are well protected.
8. Data is top secret but not encrypted
One of the most dangerous mistakes made by organizations is not encrypting sensitive data like personal information, credit cards, passwords, etc. This has inadvertently increased the risk of exposing important data of the organization and of web or application users.
9. Lack of functional-level access control
When the authentication handler is insufficient or not working, it leads to various types of website vulnerabilities known as missing functional level access control. For example - an unauthorized entity could access a URL containing sensitive information or hidden functionality etc. but the system does not have the ability to check authentication, so it is possible that the attackers will lose the right to take over the website.
10. Light attitude towards website security activities
This is the deadliest of all website security errors. Top management must have a proactive attitude towards website security, invest in a prudent manner
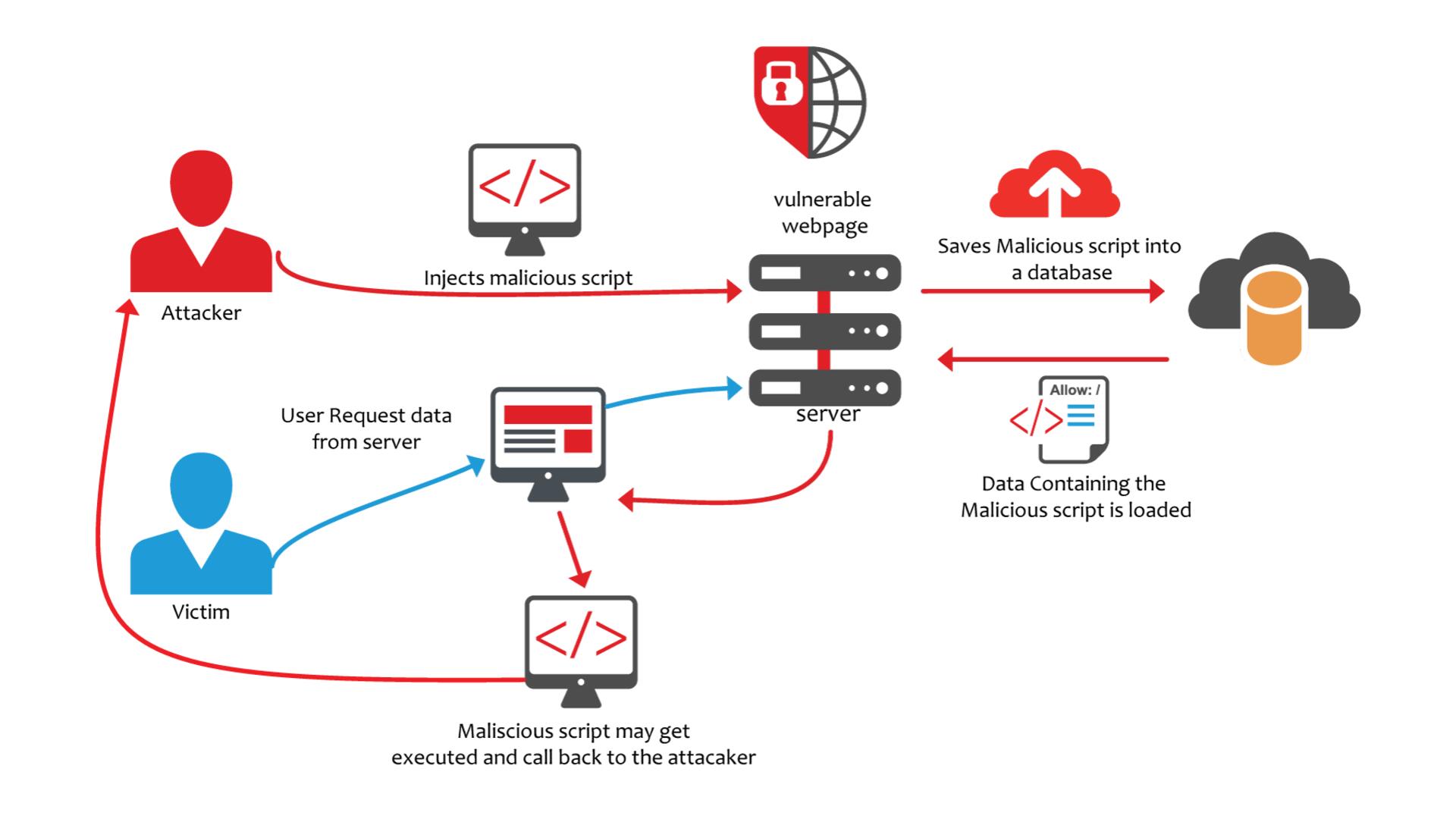
Need to use a dedicated website security solution to prevent malicious code injection attacks
Fix the website not secure
Check out our 5-step process to protect your website for website visitors:
- Install Secure Sockets Layer (SSL) Certificate
To make your HTTP site secure, you need to install an SSL certificate on your website. When you install an SSL certificate, some exchange takes place, which provides a secure version of your website to your website visitors.
- Make sure internal and external links use HTTPS
If you want both your internal and external site links to continue to work, you’ll want to make sure you change all of them to HTTPS as well. This may sound tedious, but it’s important to ensure that HTTPS helps your site instead of hurting it.
- Verify your site in Google Search Console
After installing an SSL certificate and making sure that your site links use HTTPS, you’ll want to verify both the HTTP and HTTPS versions of your site in Google Search Console. In doing so, you also want the domain to be set to the HTTPS version. This will ensure that website visitors are served a secure version of the website.
- Make sure HTTP URLs are redirected
Create a 301 redirect on your own site to make sure your HTTP URLs refer to the HTTPS version.
- Update XML sitemap
Next, you’ll want to update your XML sitemap to reference the HTTPS versions of the pages on your site. Your sitemap acts as a road map for your website visitors as well as Google to help them easily navigate your site.
WordPress website security
WordPress is the most popular Content Management System (CMS) and powers over 30% of websites. However, as it evolved, hackers took note and started targeting WordPress sites specifically. No matter what kind of content your website offers, you are not an exception. If you don’t take certain precautions, you could be attacked. Like everything related to technology, you need to check your website’s security.
In this guide, we will share the 10 Best Tips to keep your WordPress site secure:
-
Choose a good hosting company (web hosting)
-
Don’t use disabled, or locked themes
-
Install a WordPress Security Plugin
-
Use strong passwords
-
Disable file editing permission
-
Install SSL Certificate
-
Change Your WP Login URL
-
Limit the number of incorrect login attempts, allowing up to 3 wrong entries for example
-
Hide wp-config.php and .htaccess files
-
Update Your WordPress Version Regularly
How to secure a website with VNIS’s AI technology

VNIS combines the power of Multi CDN__, AI Load Balancing, and Cloud WAF for comprehensive DDoS protection
Using a smart and comprehensive website security solution like VNIS (VNETWORK Internet Security) is the right direction. The Cloud WAF firewall in VNIS helps businesses enhance web application security and provides comprehensive end-to-end website security without experiencing any false positives. The system will perform daily website scanning to prevent malicious requests/bad requests and completely remove application layer vulnerabilities (Layer 7).
VNIS also has an AI (artificial intelligence) and RUM system that continuously monitors DDoS attacks, analyzes attack patterns, and more. for quick processing. The system also combines the power of the global Multi CDN network to enhance the security of the website (Anti-DDoS attack layer 3/4), so that businesses can fully focus on business activities.
See more: What is a CDN and 6 special benefits of CDN technology
