The DDoS test is not too strange a term when starting to perfect and use a website. However, doing it the wrong way can hurt your website. Therefore, properly tested DDoS is an indispensable and essential condition to detect potential errors, check the security level of the website, access rights as well as the ability to handle the traffic. Nowadays, there are many DDoS tutorial channels for you, but it is quite complicated and can be expensive. Today, VNETWORK will summarize the simplest but most effective and especially completely free DDoS methods in the following article:
Tool DDoS
1. DDoS attack tools that hackers often use
DDoS attack tool helps hackers perform denial of service attacks to deny users access or infiltrate servers causing disruptions to websites, networks, emails, etc. Here are some commonly used DDoS attack tools:
DDoS Attack Tools : this is a tool that can be used to perform a distributed denial-of-service attack. This application can monitor logs, record events from various sources, and detect processes communicating using command and control servers.
DAVOSET : this is a great tool for performing a DDoS attack. Currently, DAVOSET has support for cookies and many other features.
Slowloris : used to build a DDoS attack. The Slowloris attack tries to keep maximum cohesion with those opened, this is achieved by sending a partial request.
HOIC : is a denial of translation attack tool designed to attach multiple files at once. This DDoS tool helps to perform DDoS attacks using the HTTP method.
2. The tools that bring down the popular Web
These tools can attack web servers directly and they are being used by many hackers:
LOIC : is open-source software and is used for DDoS attacks. LOIC is one of the free DDoS attack tools that check the performance of the network. Create an online DDoS attack that penetrates any web.
HULK : is a DDoS attack tool that generates unique requests for every request that obfuscates a website’s traffic.
PyLoris : PyLoris tool that uses SSL connection and SOCKS proxy to perform a DDoS attack on the server.
RUDY : through the post method, this tool attacks cloud applications by discarding available sessions on the web server.
DDOSIM : this tool is used to simulate real DDoS attacks. It is used to perform DDOS attacks by emulating many zombie servers. All zombie servers make TCP connections to target the target server. This is the most effective tool to knock down the Web today.
How to DDoS Web using CMD used by hackers
CMD – Command Prompt is an application used to run commands in Windows. CMD has built-in many different commands, the function of which is to operate the system only through a command input interface instead of having to operate step by step on the Windows operating system. CMD is a Windows MS-DOS (Microsoft Dos) emulator that contains many built-in commands, but it is not MS-DOS.
How to crash a website with CMD (Command Prompt):
This is a simple way to DDoS a website, just a free tool available in Windows can be done.
Step 1: Find the website IP address.
You can use this syntax in CMD to find the IP of any website.
Ping www.temien.com –t
(In which “www.tenmien.com” is the website of the subject that needs DDoS.)
If you don’t know how to open CMD, you can type “CMD” in the search box on the START bar.
Step 2: Open CMD and run the command
In CMD, type the code that crashes the website:
ping [xxx.xxx.xxx.xxx] -t -l 65500
(Where xxx.xxx.xxx.xxx is the IP address of the website to be attacked)
Step 3: Wait and Observe
Now, your job is to wait and see how the website responds to a DDoS attack.
Step 4: Done
When you visit that website and get the message “server down” or “temporary website”, the DDoS test is complete.
Note that:
-
This method only successfully attacks when knowing the IP address of the origin server.
-
The attacker’s network must be strong, otherwise, it will be “counterproductive”.
-
The more computers that do this at the same time, the more the problem becomes like an “international attack”.
The simplest way to DDoS website, but sometimes it is also difficult to succeed because the network bandwidth from the attacker side is too weak to attack.
Types of DDoS Server Games
For Game Servers, the most common DDoS attacks are layer 3 and layer 4 DDoS attacks (layer 7 if it’s a web game). Following are some types of Server Game DDoS attacks based on the most common protocols:
1. UDP Flood Attack : This is a form of Denial of Service (DoS) attack, which is an unreliable connection protocol. UDP Flood attacks typically send a large number of User Datagram Protocol (UDP) packets to the server to be attacked. When the number of requests exceeds the allowable threshold, it will lead to the loss of the ability to process user requests, at which point a denial of service will occur.
2. ICMP floods : This strategy uses false ICMP error requests to overload the network’s bandwidth.
3. SYN floods : This attack exploits the TCP handshake (3-way TCP handshake). The attacker sends TCP requests with fake IP addresses to the target. The target system responds and waits for the sender to confirm the handshake. Since the attacker never sends a response to complete the TCP handshake, the incomplete processes pile up and eventually crash the server.
4. Smurf DDoS : A hacker uses malware to create a network packet tied to a false (spoof) IP address. This packet contains an ICMP ping message asking the network to send back a response. The hacker will send a response (echo) to the network IP address back, creating an infinite loop that eventually crashes the system.
How to crash the Web on the phone that hackers often do on the Android operating system
There are many ways to DDoS attack a website by phone such as:
-
Use the phone to scan web pages for vulnerabilities with RapidScan UserLAnd. RapidScan does one thing is to automate the deployment of vulnerability scanners and web testing software. Attacks on those vulnerabilities can then be carried out with a few simple commands.
-
Use Android software, this is a tool specially designed for the Android operating system. This tool is written for testing and it has quite strong DDoS attack capabilities.
-
Termux is a tool that hackers often use to DDoS a website by phone. It emulates a command-line tool on Android that can work directly without needing to be rooted or installed.
Instructions for DDoS Website to test its security ability
Based on DDoS Tools you can easily perform a cyber attack to test the security of any website you want. Here are a few ways to flood the target server with TCP, UDP, or HTTP packets with a simple LOIC tool.
Step 1: Download LOIC (low orbit ion cannon)
LOIC can be downloaded from many different sources on google and of course, you will get a warning from your anti-virus software that there is a malicious tool… reason is that it is a DDoS tool. Later, unzip the zip file and run this software.
Step 2: Run LOIC
After starting to run, you will see your screen like below. The menu will show all options for a DDoS attack

Step 3: Set up and start a DDoS attack
In this section, LIOC allows you to set options such as configuration for network attack, target IP or URL, port, number of streams, and speed of DDoS attack.

Once you have completed the desired configurations for the DDoS attack, click the following button:
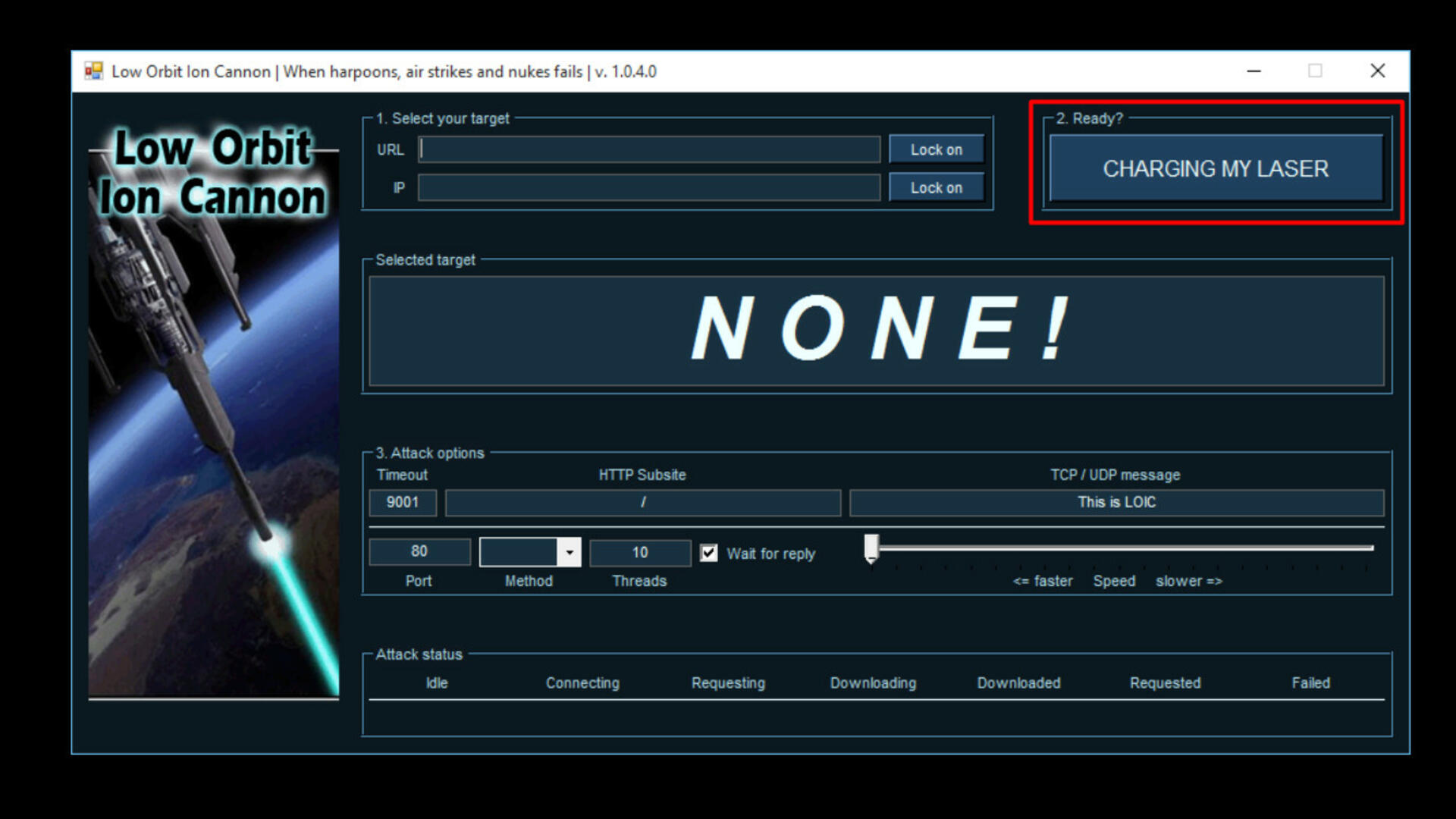
You can now see the attack status in the Attack status section.

Thus, you have finished simulating a DDoS attack on the website. However, you should test your websites because cyberattacks that leave consequences for businesses may be interfered with by law.
Web Server attacks effectively
Distributed infrastructure: The geographical distribution of servers will partly help the servers to be less affected by DDoS attacks at the same time. In addition, businesses need to ensure that they have a good load-balancing system to distribute traffic between them. DDoS server defense performance will be better if these centers are located in many different countries.
Increase bandwidth and server capacity: The main reason why websites crash or crash is because of not handling the traffic caused by DDoS attacks. Therefore, upgrading the web server will help you somewhat reduce DDoS attacks.
Using WAF and CDN: WAF can detect and prevent DDoS (layer 7) attacks by monitoring anomalous traffic and blocking their access. In addition, a CDN can balance the traffic on the website, by distributing them on different servers around the globe. At that time, it will be difficult for hackers to initiate DDoS attacks (layers 3, and 4) targeting your website.
See more: What is a CDN and 6 special benefits of CDN technology
A DDoS attack can be measured in terms of traffic and duration. At VNETWORK, we also recorded the largest DDoS attacks that consumed more than 1.6 Tbps and lasted more than an hour.
Therefore, using a single CDN can only help increase the network capacity of an enterprise’s Web Server with a bandwidth of 1-5 Tbps. Some of the more advanced CDNs can provide bandwidth levels from 10-100 Tbps.
As the scale of DDoS attacks increases, if you rely on a single CDN provider, it will be difficult to prevent DDoS attacks globally. We need to strengthen the power of CDNs through global alliance CDNs.
The Multi CDN 404 solution will help protect websites against high-volume attacks, attacks like Smurf, UDP, and even reflection DDoS attacks.
Learn more about VNIS Multi CDN 404 and effective anti-DDoS methods from VNETWORK or register for a trial of anti-DDoS service via hotline: (028) 7306 8789 or email: contact@vnetwork.vn or sales@vnetwork.vn.
